Article
May 2025 Patch Tuesday: Key Vulnerabilities Overview
Introduction
Microsoft’s May security update addresses over 70 vulnerabilities across various Windows systems, including patches for five zero-day vulnerabilities that are currently being exploited. A relatively high number of these vulnerabilities affect Microsoft Office. While only one is classified as critical, the widespread use of Office and the relative ease of exploitation make them noteworthy.
This article outlines their impact and the steps needed to secure your systems.
Summary of May 2025 Patch Tuesday
This month’s Patch Tuesday delivers a broad set of security updates, addressing vulnerabilities across widely used Microsoft software. Notably, the updates include fixes for issues in Windows, server software, and particularly Microsoft Office—tools heavily relied upon by businesses. A key concern is a vulnerability in the Windows Scripting Engine that could allow attackers to execute malicious code without user interaction. Other patches address flaws in Remote Desktop Services and server management tools. Overall, these updates underscore the importance of promptly applying patches to protect systems from known threats.
Understanding these updates is crucial in protecting enterprise environments. Below, we categorize the vulnerabilities based on their exposure to the internet.
Updates are listed according to their CVSS Score
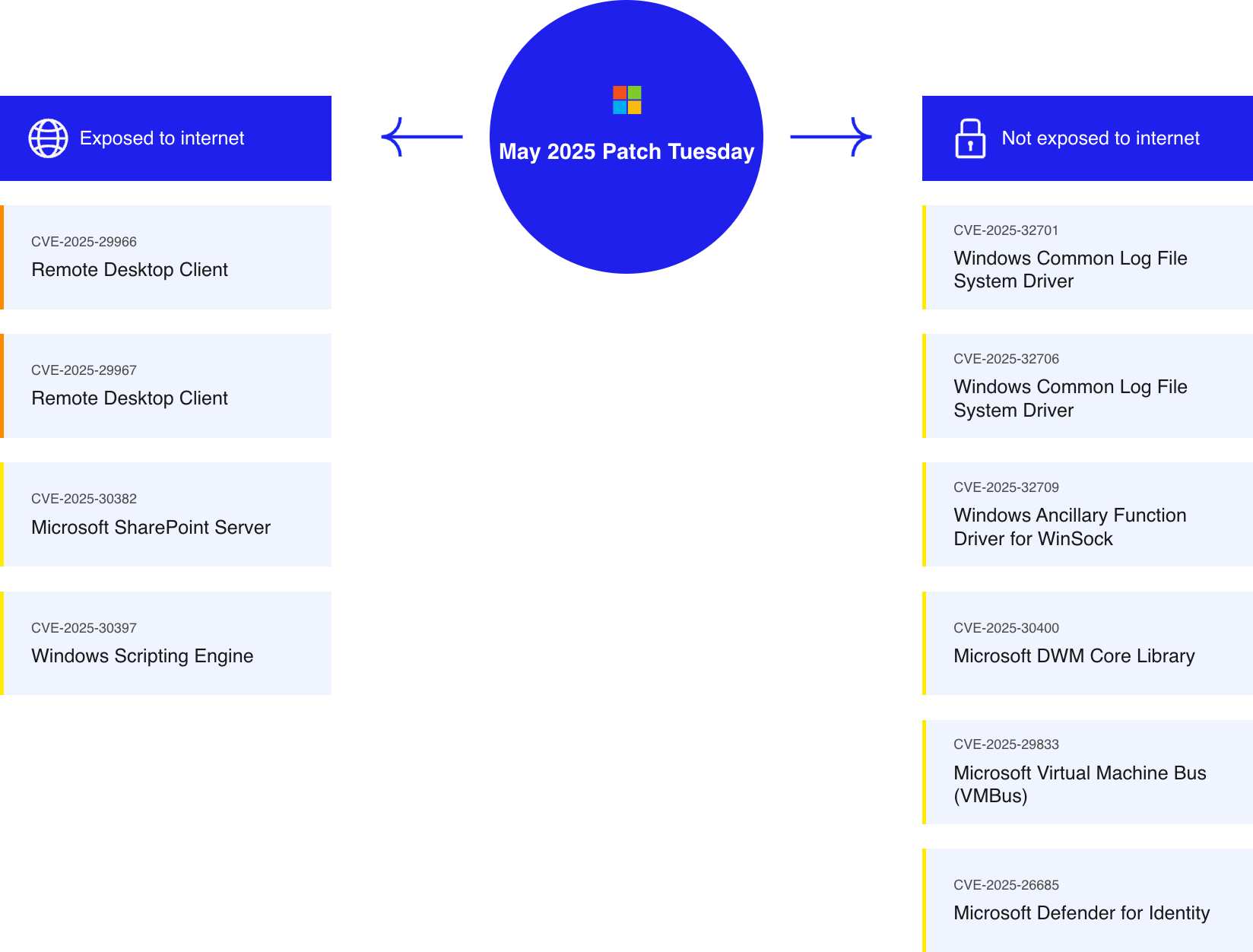
Exposed to the Internet
Remote Desktop Client – Heap-Based Buffer Overflow
A heap-based buffer overflow vulnerability exists in the Remote Desktop Client, allowing for remote code execution. This flaw can be exploited by a malicious Remote Desktop server.
Remote Desktop Client – Heap-Based Buffer Overflow
Another heap-based buffer overflow vulnerability in Remote Desktop Client, similar to CVE-2025-29966, may occur when a vulnerable client connects to a compromised or malicious RDP server.
Microsoft SharePoint Server – Remote Code Execution Vulnerability
A remote code execution vulnerability in Microsoft SharePoint Server arises from the deserialization of untrusted data. Exploitation allows threat actors to execute arbitrary code, potentially compromising the context of the SharePoint service account.
Windows Scripting Engine – Memory Corruption Vulnerability
A memory corruption vulnerability in the Windows Scripting Engine can allow for remote code execution if a user clicks on a specially crafted URL. This vulnerability is particularly associated with Microsoft Edge operating in Internet Explorer mode and has specific conditions that prevent widespread exploitation.
Internal Network
Windows Common Log File System Driver – Use-After-Free Vulnerability
A use-after-free vulnerability in the Windows Common Log File System (CLFS) driver could allow authenticated attackers to gain SYSTEM privileges. CLFS is utilized by various applications, and this vulnerability has been actively exploited.
Windows Common Log File System Driver – Improper Input Validation
An improper input validation vulnerability in the CLFS driver permits privilege escalation to SYSTEM. This issue has been actively exploited and bears similarities to CVE-2025-32701.
Windows Ancillary Function Driver for WinSock – Use-After-Free Vulnerability
A use-after-free vulnerability in the Windows Ancillary Function Driver for WinSock allows attackers to elevate their privileges to Administrator level. This driver facilitates low-level network communications in Windows.
Microsoft DWM Core Library – Zero-Day Vulnerability
A zero-day vulnerability in the Desktop Window Manager Core Library allows attackers to elevate privileges to SYSTEM. DWM handles the display of visual elements on Windows PCs, and exploitation of this vulnerability has been reported.
Microsoft Virtual Machine Bus (VMBus) – Race Condition
A race condition in Microsoft Virtual Machine Bus (VMBus) can allow authenticated attackers to execute code remotely. VMBus serves as the communication conduit between parent and child partitions within the Hyper-V environment.
Microsoft Defender for Identity – Spoofing Vulnerability
A spoofing vulnerability in Microsoft Defender for Identity could allow attackers with LAN access to perform spoofing. This cloud-based security solution is integral in monitoring and securing identities.
Conclusion
In summary, May 2025’s Patch Tuesday highlights the ongoing risks posed by software vulnerabilities in widely used systems. Keeping systems up to date is one of the most effective ways to reduce the risk of exploitation. We strongly recommend that all users and organizations apply the latest patches promptly to maintain security.
Have questions about implementing these patches or securing your IT environment? Schedule a call with At-Bay’s Advisory Services team to get started.
About CVSS
The Common Vulnerability Scoring System (CVSS) is an industry-standard framework for evaluating and communicating the severity of software vulnerabilities. It provides a numerical score that helps organizations prioritize and address security issues effectively. CVSS scores quantify the severity of a vulnerability on a scale from 0 (no severity) to 10 (critical severity). CVSS considers multiple factors, including; Exploitability, Impact, Exploit code maturity, Remediation level, Report confidence. The system enables organizations to compare and prioritize vulnerabilities based on their potential impact on IT infrastructure.
References
- https://msrc.microsoft.com/update-guide/releasenote/2025-may
- https://www.helpnetsecurity.com/2025/05/13/patch-tuesday-microsoft-fixes-5-actively-exploited-zero-days/
- https://blog.talosintelligence.com/microsoft-patch-tuesday-for-may-2025-snort-rules-and-prominent-vulnerabilities/
- https://www.rapid7.com/blog/post/2025/05/13/patch-tuesday-may-2025/
- https://www.bleepingcomputer.com/news/microsoft/windows-11-kb5058411-and-kb5058405-cumulative-updates-released/
- https://community.spiceworks.com/t/today-s-patch-tuesday-overview-70-vulnerabilities-5-zero-days-5-critical-and-two-with-pocs/1205367
- https://www.tripwire.com/state-of-security/may-2025-patch-tuesday-analysis
- https://blog.qualys.com/vulnerabilities-threat-research/2025/05/13/microsoft-patch-tuesday-may-2025-security-update-review