Article
June 2025 Patch Tuesday: Key Vulnerabilities Overview
Introduction
Microsoft’s June security update addresses more than 66 vulnerabilities across various Windows systems. Several of these flaws allow remote code execution and could be exploited by attackers to compromise your business. In this article, we provide an overview of the patches and highlight the most critical updates that require immediate attention.
Summary of June 2025 Patch Tuesday
In June, Microsoft released updates to fix 66 security vulnerabilities, including several critical issues that could allow remote attackers to take control of affected devices. One notable flaw involves the WebDAV protocol, commonly used for online file sharing, while another targets Microsoft SharePoint, a widely used business collaboration tool. If left unpatched, these vulnerabilities could expose sensitive data or disrupt system functionality.
Understanding these updates is crucial in protecting enterprise environments. Below, we categorize the vulnerabilities based on their exposure to the internet.
Updates are listed according to their CVSS Score
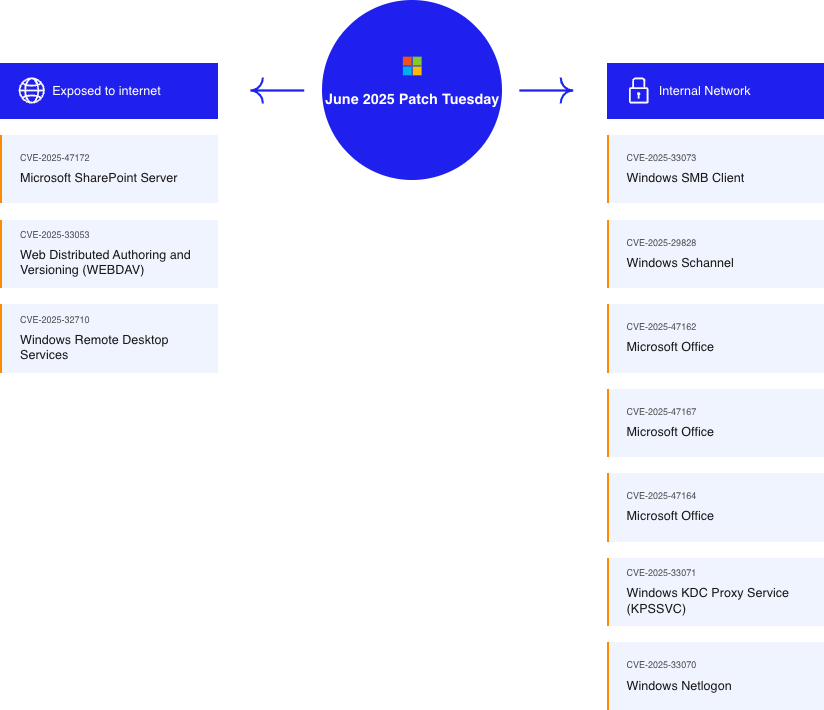
Exposed to the Internet
Microsoft SharePoint Server – Remote Code Execution
Microsoft SharePoint Server is vulnerable to remote code execution due to improper neutralization of SQL commands. This flaw can be exploited by authenticated users, posing significant security risks in document management and web-based collaboration.
Web Distributed Authoring and Versioning (WEBDAV) – Remote Code Execution
WebDAV, a protocol used for web-based collaborative content authoring, has a remote code execution vulnerability. Attackers can exploit this flaw by controlling filenames or paths in WebDAV implementations to execute arbitrary code remotely.
Windows Remote Desktop Services – Use-after-free
A use-after-free vulnerability in Windows Remote Desktop Services poses a risk for unauthenticated remote code execution. This vulnerability impacts remote desktop connections, a key feature for remote system administration.
Internal Network
Windows SMB Client – Elevation of Privilege
The Windows SMB Client, a critical network file-sharing protocol, contains an elevation of privilege vulnerability. This flaw allows attackers with low privileges to exploit improper access control and potentially gain SYSTEM-level access.
Windows Cryptographic Services (Schannel) – Remote Code Execution
The Windows Schannel, implementing SSL and TLS protocols, has a memory leak vulnerability leading to remote code execution. This vulnerability allows attackers to execute malicious code over the network, compromising secure communications.
Microsoft Office – Heap-based Buffer Overflow
A vulnerability in Microsoft Office, a widely-used suite of productivity applications, enables remote code execution through heap-based buffer overflow. This flaw can be exploited through locally triggered attacks, posing significant risk to users.
Microsoft Office – Type Confusion
Microsoft Office faces a type confusion issue that could allow attackers to execute malicious code remotely. Given its expansive use for business productivity, this flaw poses significant threats to user data and security.
Microsoft Office – Use-after-free
A use-after-free vulnerability in Microsoft Office allows attackers to execute remote code by exploiting malicious documents. This issue threatens document creation, collaboration, and sharing functionalities of the Office suite.
Windows KDC Proxy Service (KPSSVC) – Remote Code Execution
A security weakness in the cryptographic protocol of Windows KDC Proxy Service allows for remote code execution. KPSSVC facilitates HTTPS-encrypted communication between clients and KDC servers, so this vulnerability could undermine secure communication.
Windows Netlogon – Elevation of Privilege
A vulnerability in the Netlogon service of Windows allows elevation of privilege due to uninitialized resource use. This flaw can enable attackers to potentially gain domain administrator privileges, critically affecting domain authentication and communication.
Conclusion
The June 2025 Patch Tuesday update impacts many widely used systems, underscoring the importance of keeping devices up to date. Applying security updates promptly is one of the most effective ways to minimize the risk of exploitation. We strongly encourage all users and organizations to install the latest patches without delay to ensure their systems remain secure.
Have questions about implementing these patches or securing your IT environment? Schedule a call with At-Bay’s Advisory Services team to get started.
About CVSS
The Common Vulnerability Scoring System (CVSS) is an industry-standard framework for evaluating and communicating the severity of software vulnerabilities. It provides a numerical score that helps organizations prioritize and address security issues effectively. CVSS scores quantify the severity of a vulnerability on a scale from 0 (no severity) to 10 (critical severity). CVSS considers multiple factors, including; Exploitability, Impact, Exploit code maturity, Remediation level, Report confidence. The system enables organizations to compare and prioritize vulnerabilities based on their potential impact on IT infrastructure.
References
- https://msrc.microsoft.com/update-guide/releasenote/2025-jun
- https://isc.sans.edu/diary/microsoft+patch+tuesday+june+2025/32032/
- https://www.bleepingcomputer.com/news/microsoft/microsoft-june-2025-patch-tuesday-fixes-exploited-zero-day-66-flaws/
- https://www.hackread.com/june-2025-patch-tuesday-microsoft-bugs-active-0-day/
- https://blog.qualys.com/vulnerabilities-threat-research/2025/06/10/microsoft-and-adobe-patch-tuesday-june-2025-security-update-review
- https://www.computerweekly.com/news/366625818/June-Patch-Tuesday-brings-a-lighter-load-for-defenders
- https://www.crowdstrike.com/en-us/blog/patch-tuesday-analysis-june-2025/
- https://blog.talosintelligence.com/microsoft-patch-tuesday-june-2025/
- https://www.rapid7.com/blog/post/2025/06/10/patch-tuesday-june-2025/