Article
July 2025 Patch Tuesday: Key Vulnerabilities Overview
Introduction
Microsoft’s July security update addresses over 100 vulnerabilities, including several critical issues. Many of these flaws, particularly those allowing remote code execution and affecting platforms like SQL Servers and SharePoint, could be exploited by attackers to compromise your business. Importantly, some of these vulnerabilities are potentially exploitable over the internet, making prompt updates essential. In this article, we provide an overview of this month’s patches and highlight the most notable security issues that require immediate attention.
Summary of July 2025 Patch Tuesday
This July, Microsoft tackled over 100 vulnerabilities, or security weaknesses, including several that are deemed critical. The main focus this month is on securing systems that might be targeted by cyberattacks, such as SQL Servers and SharePoint platforms used by businesses. Importantly, some of these vulnerabilities could potentially be exploited over the internet, making it even more essential to update them promptly. With a combination of fixes affecting systems that many businesses rely on and those that are simply common in home use, July’s Patch Tuesday underlines the importance of staying current on software updates to maintain security.
Understanding these updates is crucial in protecting enterprise environments. Below, we categorize the vulnerabilities based on their exposure to the internet.
Updates are listed according to their CVSS Score
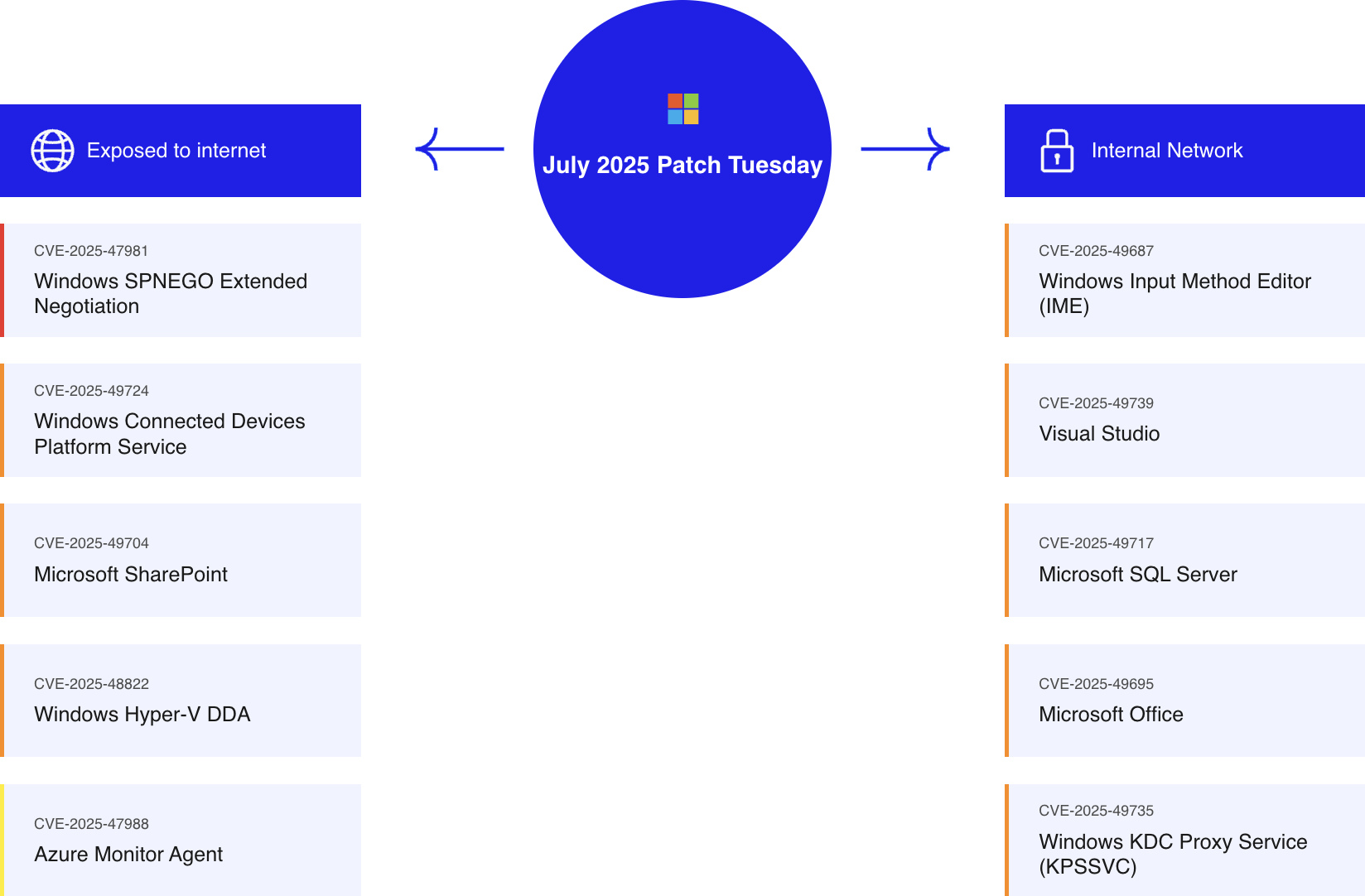
Exposed to the Internet
Windows SPNEGO Extended Negotiation – Remote Code Execution
This critical vulnerability in the Windows SPNEGO Extended Negotiation (NEGOEX) mechanism allows unauthenticated remote attackers to execute arbitrary code via a heap-based buffer overflow. SPNEGO is a significant authentication protocol in Windows and enterprise systems, making this vulnerability particularly concerning.
Windows Connected Devices Platform Service – Remote Code Execution
This vulnerability affects the Connected Devices services on Windows systems, allowing arbitrary code execution via specially crafted packets targeting TCP port 5040. Its exploitation can significantly impact device connectivity and network security.
Microsoft SharePoint – Remote Code Execution
With this critical vulnerability, attackers with Site Owner privileges on Microsoft SharePoint can execute arbitrary code by exploiting code injection flaws. The ease of remote exploitation of this flaw raises significant concerns for SharePoint server security.
Windows Hyper-V DDA – Remote Code Execution
An out-of-bounds read vulnerability in Windows Hyper-V DDA allows unauthenticated attackers to execute code, typically involving tricking users into importing malicious INF files. This can impact host systems from a virtual machine, posing threats to virtualized environments.
Azure Monitor Agent – Remote Code Execution
This flaw in Azure Monitor Agent allows remote code execution over an adjacent network, compromising systems where the agent is installed. It poses a risk for networked systems using Azure’s monitoring service.
Internal Network
Windows Input Method Editor (IME) – Elevation of Privilege
By exploiting a vulnerability in the Windows Input Method Editor (IME), attackers can elevate their privileges from low to medium integrity, enabling additional malicious activities on Windows operating systems.
Visual Studio – Elevation of Privilege
An elevation of privilege vulnerability in Visual Studio enables attackers to execute code with elevated privileges within the development environment. Exploiting this flaw requires local access but threatens the security of development processes.
Microsoft SQL Server – Remote Code Execution
This vulnerability affects Microsoft SQL Server, including instances running on-premises and in Windows Azure environments. Authenticated attackers with low privileges can exploit a heap-based buffer overflow to execute arbitrary code, posing a threat to database security.
Microsoft Office – Remote Code Execution
A use-after-free vulnerability in Microsoft Office allows unauthenticated attackers to execute arbitrary code through the preview pane. This vulnerability is particularly severe as it can be triggered without user interaction, impacting the widespread Office suite.
Windows KDC Proxy Service (KPSSVC) – Remote Code Execution
This vulnerability in the Kerberos KDC Proxy Service allows unauthenticated remote attackers to execute arbitrary code due to a use-after-free flaw. It specifically impacts Windows servers configured as KDC Proxy Protocol servers, excluding domain controllers.
Conclusion
The July 2025 Patch Tuesday update impacts many widely used systems, underscoring the importance of keeping devices up to date. Applying security updates promptly is one of the most effective ways to minimize the risk of exploitation. We strongly encourage all users and organizations to install the latest patches without delay to ensure their systems remain secure.
Have questions about implementing these patches or securing your IT environment? Schedule a call with At-Bay’s Advisory Services team to get started.
About CVSS
The Common Vulnerability Scoring System (CVSS) is an industry-standard framework for evaluating and communicating the severity of software vulnerabilities. It provides a numerical score that helps organizations prioritize and address security issues effectively. CVSS scores quantify the severity of a vulnerability on a scale from 0 (no severity) to 10 (critical severity). CVSS considers multiple factors, including; Exploitability, Impact, Exploit code maturity, Remediation level, Report confidence. The system enables organizations to compare and prioritize vulnerabilities based on their potential impact on IT infrastructure.
References
- https://msrc.microsoft.com/update-guide/releasenote/2025-jul
- https://blog.talosintelligence.com/microsoft-patch-tuesday-july-2025/
- https://www.zerodayinitiative.com/blog/2025/7/8/the-july-2025-security-update-review
- https://www.rapid7.com/blog/post/patch-tuesday-july-2025/
- https://www.crowdstrike.com/en-us/blog/patch-tuesday-analysis-july-2025/