Article
January 2025 Patch Tuesday: Key Vulnerabilities Overview
Introduction
Microsoft has released its first security update package for 2025, addressing 159 vulnerabilities across 13 product families in this month’s Patch Tuesday. While the number of patches is significant, this article breaks them down to help you understand their impact and the steps needed to secure your systems.
Summary of January 2025 Patch Tuesday
Microsoft’s January 2025 Patch Tuesday addresses 159 vulnerabilities across multiple platforms, with 10 classified as critical. This release highlights remote code execution (RCE) vulnerabilities and privilege escalation flaws, which pose significant risks. Notably, some vulnerabilities affect internet-facing applications and services, increasing their likelihood of exploitation. These updates underscore the urgent steps users and administrators must take to mitigate potential threats and secure their systems.
Updates are listed according to their CVSS Score
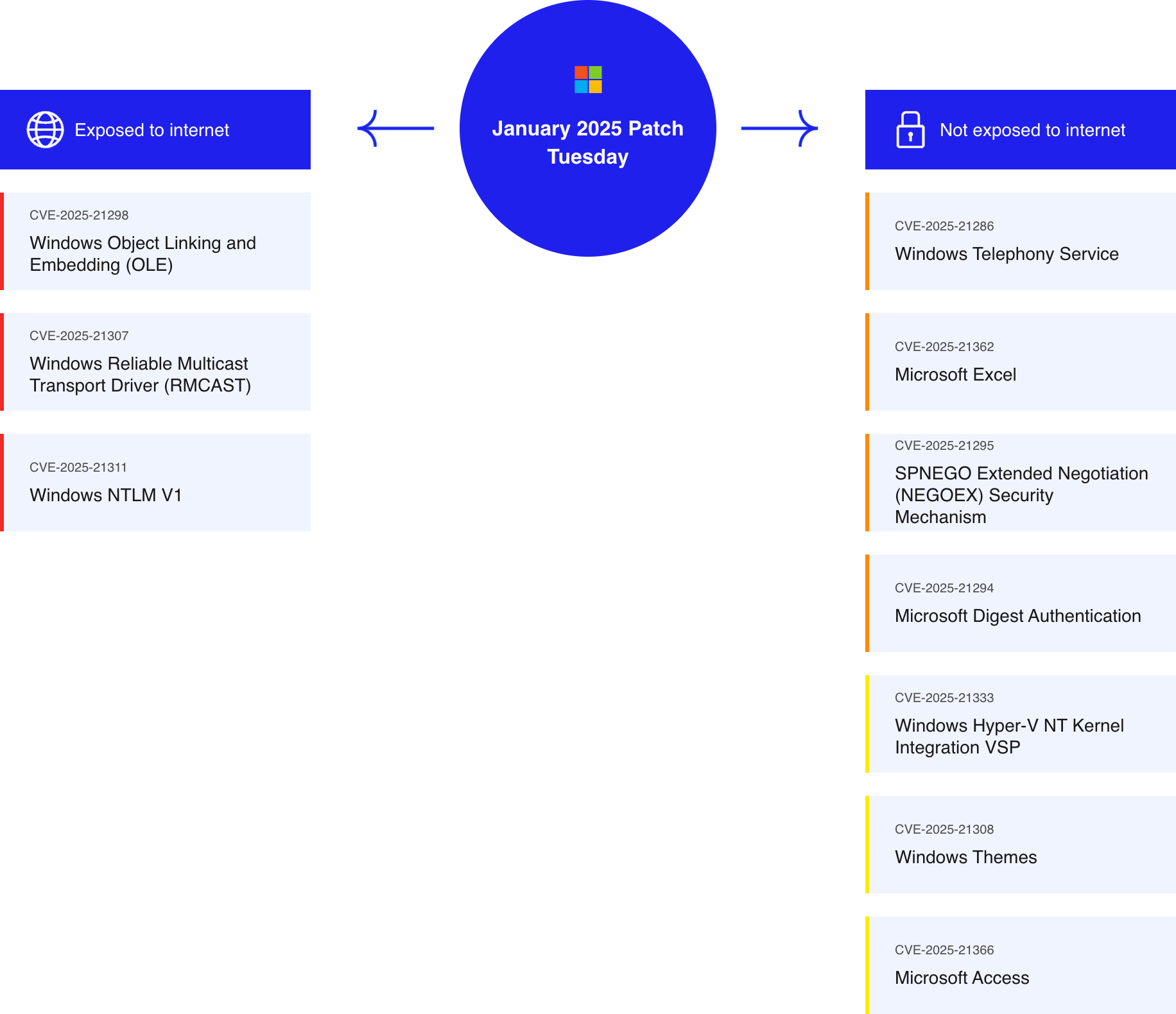
Exposed to the Internet
Windows Object Linking and Embedding (OLE) – Remote Code Execution
OLE is a Microsoft technology for embedding and linking to documents and other objects. This CVE details a critical remote code execution vulnerability where reading malicious emails, or even reviewing an attachment could trigger the code execution can trigger code execution in v, allowing attackers to execute arbitrary code.
Windows Reliable Multicast Transport Driver (RMCAST) – Remote Code Execution
RMCAST handles multicast network traffic on Windows systems. A critical vulnerability allows for code execution through specially crafted packets, which can execute remote code, representing a severe security risk.
Windows NTLM V1 – Elevation of Privilege
This CVE addresses a critical elevation of privilege vulnerability in NTLMv1, a Microsoft protocol suite, potentially allowing remote exploitation to increase access privileges within a system.
Internal Network
Windows Telephony Service – Remote Code Execution
This CVE involves a remote code execution vulnerability in Windows Telephony Service, which manages telephony-based communications. Though less likely to be exploited, it still represents a potential threat for remote attacks.
Microsoft Excel – Remote Code Execution
Microsoft Excel, a spreadsheet application, is susceptible to a critical remote code execution vulnerability that can be triggered via the preview pane, emphasizing the need for heightened caution when managing Excel files.
SPNEGO Extended Negotiation (NEGOEX) Security Mechanism – Remote Code Execution
This critical vulnerability affects the NEGOEX security mechanism within SPNEGO, a Windows application protocol for negotiating security technology, allowing remote code execution without user interaction.
Microsoft Digest Authentication – Remote Code Execution
The vulnerability in Microsoft Digest Authentication protocol allows for remote code execution by exploiting a race condition, affecting systems’ authentication processes over HTTP/HTTPS.
Windows Hyper-V NT Kernel Integration VSP – Elevation of Privilege
Hyper-V is a virtualization system from Microsoft, and the NT Kernel integration supports communication between guest and host systems. This vulnerability allows attackers to elevate privileges to SYSTEM on compromised Windows and Windows Server machines, posing significant security risks.
Windows Themes – Spoofing
Windows Themes permit desktop personalization and are vulnerable to a spoofing attack that could result in the improper disclosure of an NTLM hash, posing privacy risks.
Microsoft Access – Remote Code Execution
Microsoft Access is a database management system that faces a vulnerability enabling remote code execution when a malicious file is opened, significantly impacting data security and integrity.
Conclusion
January 2025’s Patch Tuesday introduces critical updates affecting Microsoft’s core systems and products, including the popular Office products- Excel and Access. The rising number of vulnerabilities each month reflects the increasing complexity and pace of modern cyber threats. To safeguard networks and data, businesses must prioritize and apply these updates without delay.
Have questions about implementing these patches or securing your IT environment? Schedule a call with At-Bay’s Advisory Services team to get started.
About CVSS
The Common Vulnerability Scoring System (CVSS) is an industry-standard framework for evaluating and communicating the severity of software vulnerabilities. It provides a numerical score that helps organizations prioritize and address security issues effectively. CVSS scores quantify the severity of a vulnerability on a scale from 0 (no severity) to 10 (critical severity). CVSS considers multiple factors, including; Exploitability, Impact, Exploit code maturity, Remediation level, Report confidence. The system enables organizations to compare and prioritize vulnerabilities based on their potential impact on IT infrastructure.
Read More
- https://msrc.microsoft.com/update-guide/releaseNote/2025-jan
- https://community.spiceworks.com/t/the-first-patch-tuesday-of-2025-is-here/1163231
- https://blog.talosintelligence.com/january-patch-tuesday-release/
- https://www.rapid7.com/blog/post/2025/01/14/patch-tuesday-january-2025/
- https://www.helpnetsecurity.com/2025/01/14/january-2025-patch-tuesday-microsoft-hyper-v-zero-day-cve-2025-21333-cve-2025-21334-cve-2025-21335/
- https://www.zerodayinitiative.com/blog/2025/1/14/the-january-2025-security-update-review