Article
February 2025 Patch Tuesday: Key Vulnerabilities Overview
Introduction
Microsoft has released its second security update of 2025, addressing 56 vulnerabilities, including two zero-days, in this month’s Patch Tuesday. While fewer patches were issued compared to January, several critical vulnerabilities remain, including two vulnerabilities which are known to be exploited. This article explains their impact and the steps needed to secure your systems.
Summary of February 2025 Patch Tuesday
February 2025 Patch Tuesday addressed a variety of vulnerabilities across Microsoft products. The update tackled issues ranging from remote code execution in widely used software to more specific vulnerabilities related to low-level system drivers. Two of these have been listed at CISA Known Exploited Vulnerabilities Catalog due to their severity.
Understanding these updates is crucial in protecting enterprise environments. Below, we categorize the vulnerabilities based on their exposure to the internet.
Updates are listed according to their CVSS Score
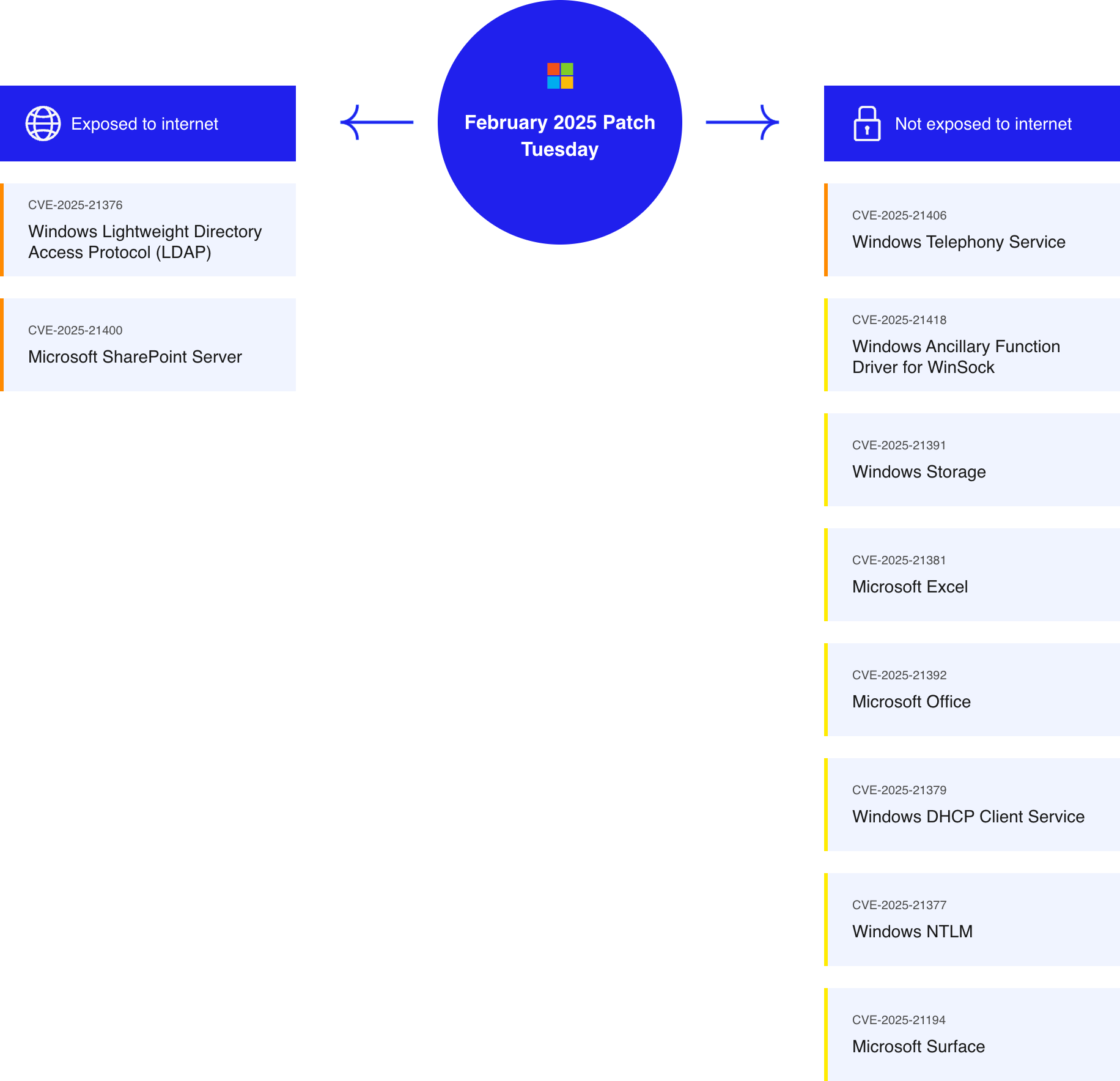
Exposed to the Internet
Windows Lightweight Directory Access Protocol (LDAP) – Remote Code Execution
LDAP is a standard network protocol used to access directory services. A remote code execution vulnerability allows unauthenticated attackers to execute arbitrary code by sending a specially crafted request to a vulnerable LDAP server. Successful exploitation may trigger a buffer overflow, potentially leading to remote code execution.
Microsoft SharePoint Server – Remote Code Execution
A remote code execution vulnerability in Microsoft SharePoint Server could allow code execution, affecting the web-based collaborative platform integrated with Microsoft Office.
Internal Network
Windows Telephony Service – Remote Code Execution
The Telephony Service enables applications to utilize telephony and messaging resources from network servers. This remote code execution vulnerability in Windows Telephony Service requires user interaction, and could result in the server returning malicious data that might cause arbitrary code execution on the user’s system.
Windows Ancillary Function Driver for WinSock – Elevation of Privilege
An elevation of privilege vulnerability in the Windows Ancillary Function Driver for WinSock allows an attacker to gain SYSTEM privileges via a heap-based buffer overflow. This vulnerability affects the component responsible for handling network-related functions. This vulnerability is known to be actively exploited by attackers (read more).
Windows Storage – Elevation of Privilege
This vulnerability in Windows Storage allows an attacker to delete targeted files on a system. Although it does not enable data disclosure, it can disrupt services. Windows Storage is crucial for managing how data is stored on a computer. This vulnerability is known to be actively exploited by attackers (read more).
Microsoft Excel – Remote Code Execution
The vulnerability allows an attacker to execute code remotely by using social engineering to trick a user into downloading and opening a specially crafted Excel file—or even just previewing it via the Preview Pane.
Microsoft Office – Remote Code Execution
In Microsoft Office, a remote code execution vulnerability allows an attacker to run arbitrary code. Microsoft Office is a suite of productivity applications including Word, Excel, and PowerPoint.
Windows DHCP Client Service – Remote Code Execution
The remote code execution vulnerability in Windows DHCP Client Service necessitates a machine-in-the-middle attack. It affects systems on the same network segment, responsible for obtaining network configurations from a DHCP server.
Windows NTLM – Spoofing
This spoofing vulnerability in Windows NTLM allows disclosure of a user’s NTLMv2 hash. It could enable an attacker to authenticate as the user. triggering this vulnerability would require minimal user interaction with a malicious file such as selecting (single-click), inspecting (right-click), or performing an action other than opening or executing the file.
Microsoft Surface – Security Feature Bypass
This security feature bypass vulnerability affects Microsoft Surface devices, which are touch-based personal computers and interactive whiteboards running Windows.
Conclusion
February 2025’s Patch Tuesday highlights the ongoing challenges in maintaining cybersecurity posture. This monthly update remains a vital touchpoint for system administrators and users to protect their environments. It’s critical to stay informed and proactive, ensuring systems are patched and secure against known vulnerabilities.
Have questions about implementing these patches or securing your IT environment? Schedule a call with At-Bay’s Advisory Services team to get started.
About CVSS
The Common Vulnerability Scoring System (CVSS) is an industry-standard framework for evaluating and communicating the severity of software vulnerabilities. It provides a numerical score that helps organizations prioritize and address security issues effectively. CVSS scores quantify the severity of a vulnerability on a scale from 0 (no severity) to 10 (critical severity). CVSS considers multiple factors, including; Exploitability, Impact, Exploit code maturity, Remediation level, Report confidence. The system enables organizations to compare and prioritize vulnerabilities based on their potential impact on IT infrastructure.
Read More
- https://msrc.microsoft.com/update-guide/releaseNote/2025-Feb
- https://krebsonsecurity.com/2025/02/microsoft-patch-tuesday-february-2025-edition/
- https://community.spiceworks.com/t/patch-tuesday-february-2025-edition/1174075
- https://www.crowdstrike.com/content/crowdstrike-www/locale-sites/us/en-us/blog/patch-tuesday-analysis-february-2025.html
- https://www.helpnetsecurity.com/2025/02/11/microsoft-fixes-exploited-zero-days-cve-2025-21418-cve-2025-21391-patch-tuesday/
- https://www.thezdi.com/blog/2025/2/11/the-february-2025-security-update-review
- https://www.tripwire.com/state-of-security/vert-threat-alert-february-2025-patch-tuesday-analysis
- https://blog.qualys.com/vulnerabilities-threat-research/2025/02/11/microsoft-patch-tuesday-february-2025-security-update-review
- https://www.rapid7.com/blog/post/2025/02/11/microsoft-patch-tuesday/