Article
December 2024 Patch Tuesday: Key Vulnerabilities Overview
Introduction
Welcome to our first Patch Tuesday Key Vulnerabilities Overview!
Microsoft Patch Tuesday for December 2024 brings a series of important security updates for various products. This monthly update focuses on addressing several critical and non-critical vulnerabilities affecting both internet-exposed and internal services. In this article, we simplify these updates to help you understand the impacts and necessary actions for keeping your systems secure.
Summary of December 2024 Patch Tuesday
This month, Microsoft released updates for multiple vulnerabilities in products such as Windows Lightweight Directory Access Protocol (LDAP), Windows Remote Desktop Services, Microsoft Message Queuing, and more. These vulnerabilities have varied scores on the Common Vulnerability Scoring System (CVSS), reflecting their potential impact severity. Some are deemed critical with remote code execution abilities, while others allow for privilege escalation.
Updates are listed according to their CVSS Score
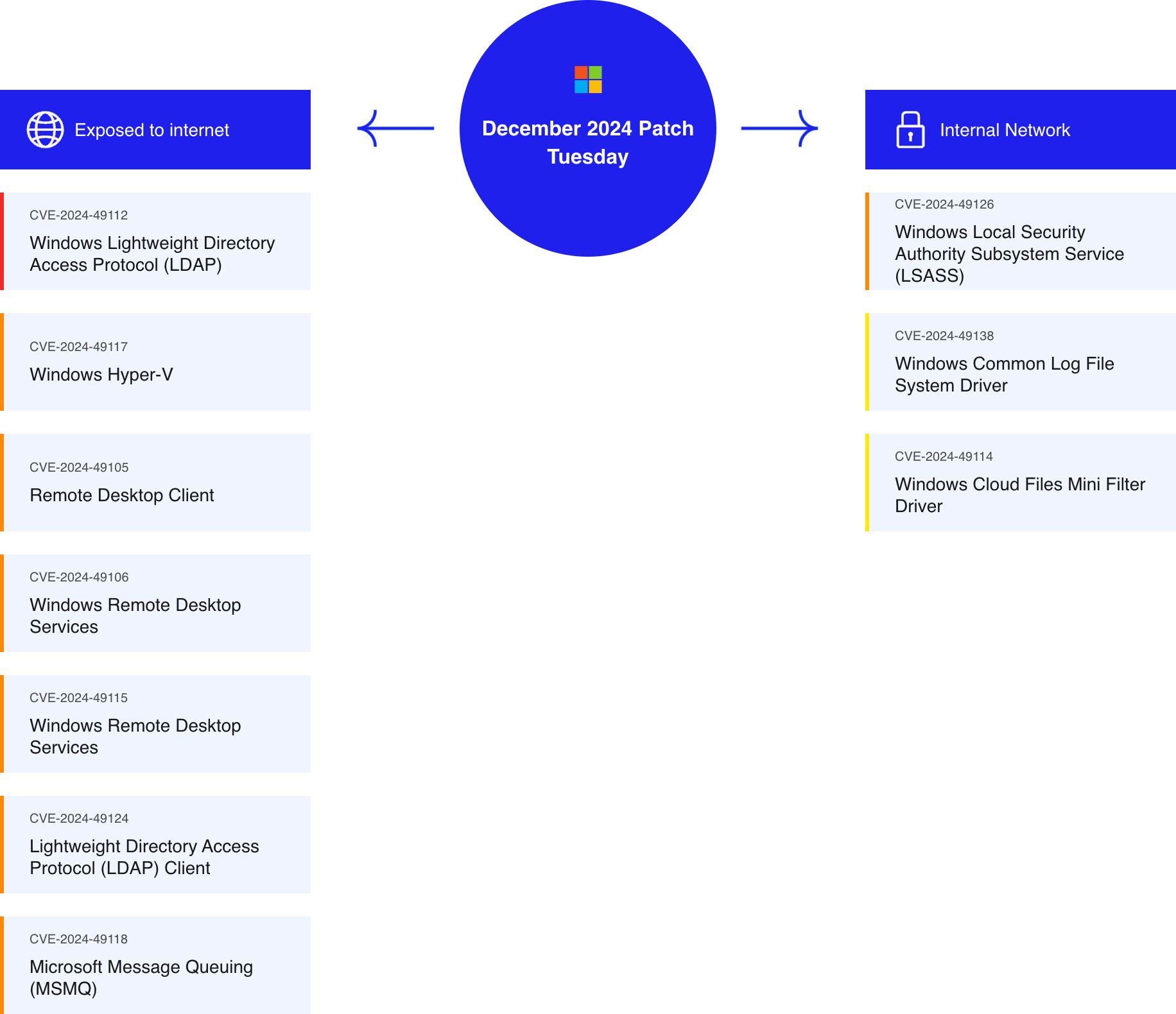
Exposed to the Internet
Windows LDAP – Remote Code Execution
This critical vulnerability affects Windows LDAP, a protocol essential for domain functionality on Windows networks. Unauthenticated attackers can exploit LDAP servers by sending specially crafted requests, potentially executing arbitrary code within the context of the LDAP service, which could compromise network security significantly.
Windows Hyper-V – Remote Code Execution
This critical vulnerability affects Microsoft’s Hyper-V virtualization technology. An attacker operating on a guest VM can exploit specially crafted file operation requests to execute code on the host OS. This threatens the security of virtualized environments by potentially compromising the host and other VMs.
Remote Desktop Client – Remote Code Execution
This critical vulnerability affects the Remote Desktop Client on Windows, where a flaw allows remote code execution via a remote desktop connection. As the client facilitates connections to remote machines, this vulnerability could lead to unauthorized access and control of remote systems, posing a threat to secure remote work environments.
Windows Remote Desktop Services – Remote Code Execution
This is a critical vulnerability in Windows Remote Desktop Services. A Remote Desktop Gateway Role can be used to trigger race condition and allow execution of arbitrary code, potentially enabling attackers to remotely execute malicious code, compromising the security of the virtual desktop and applications infrastructure.
Windows Remote Desktop Services – Remote Code Execution
This critical vulnerability in Windows Remote Desktop Services allows remote code execution via misconfigurations in the Remote Desktop Gateway service. It poses a significant risk by potentially enabling attackers to remotely execute malicious code, compromising the security of the virtual desktop and applications infrastructure.
Windows LDAP – Remote Code Execution
This critical vulnerability impacts Windows LDAP by exploiting a race condition that unauthenticated attackers can remotely utilize. This flaw can lead to severe security implications by allowing arbitrary code execution in systems that rely on LDAP for directory-based authentications and resource sharing.
Microsoft Message Queuing (MSMQ) – Remote Code Execution
This critical vulnerability affects MSMQ, a protocol for server communication. Remote attackers can exploit it by sending specially crafted MSMQ packets to a server, potentially enabling malicious code execution and compromising the security and reliability of communication between separate server applications.
Internal Network
Windows Local Security Authority Subsystem Service (LSASS) – Remote Code Execution
This vulnerability in LSASS targets server accounts through complex network calls, requiring a high complexity race condition to exploit. LSASS is critical for enforcing security policy and managing authentication in Windows, thus any compromise could have serious implications for system security and data integrity.
Windows Common Log File System Driver – Privilege Escalation
This vulnerability in the Windows Common Log File System Driver is actively being exploited as a zero-day. It allows attackers to gain SYSTEM-level permissions, leading to privilege escalation, which could let malicious actors take full control over an affected system. The CLFS driver is vital for managing log data in Windows systems.
Windows Cloud Files Mini Filter Driver – Privilege Escalation
This vulnerability allows attackers to gain escalated privileges within Windows systems. By exploiting the Cloud Files Mini Filter Driver, which syncs local files with cloud data services, attackers could potentially seize control of affected systems, posing a serious threat to user data and system integrity.
Conclusion
December 2024 Patch Tuesday tackles both current and emerging security threats across a broad range of products. With vulnerabilities impacting critical areas like directory services and virtualization platforms, it is vital for businesses to apply these updates promptly to safeguard their networks and data.
Have questions about implementing these patches or securing your IT environment? Schedule a call with At-Bay’s Advisory Services team to get started.
About CVSS
The Common Vulnerability Scoring System (CVSS) is an industry-standard framework for evaluating and communicating the severity of software vulnerabilities. It provides a numerical score that helps organizations prioritize and address security issues effectively. CVSS scores quantify the severity of a vulnerability on a scale from 0 (no severity) to 10 (critical severity). CVSS considers multiple factors, including; Exploitability, Impact, Exploit code maturity, Remediation level, Report confidence. The system enables organizations to compare and prioritize vulnerabilities based on their potential impact on IT infrastructure.
Read More
- https://msrc.microsoft.com/update-guide/releaseNote/2024-Dec
- https://community.spiceworks.com/t/december-patch-tuesday-updates-with-action1-arrow-right/1152256
- https://www.bleepingcomputer.com/news/microsoft/microsoft-december-2024-patch-tuesday-fixes-1-exploited-zero-day-71-flaws/
- https://www.helpnetsecurity.com/2024/12/10/december-2024-patch-tuesday-microsoft-zero-day-cve-2024-49138/
- https://www.zerodayinitiative.com/blog/2024/12/10/the-december-2024-security-update-review
- https://blog.talosintelligence.com/december-patch-tuesday-release/
- https://www.tripwire.com/state-of-security/vert-threat-alert-december-2024-patch-tuesday-analysis