Article
April 2025 Patch Tuesday: Key Vulnerabilities Overview
Introduction
Every month, Microsoft releases critical updates to address various vulnerabilities that could impact the security of your systems. The April 2025 Patch Tuesday focuses on vulnerabilities that can either be exploited via the internet or those that might not be exposed but still require attention to ensure enterprise security.
Summary of April 2025 Patch Tuesday
The April security update package addresses 126 vulnerabilities, with a strong focus on issues affecting internet-facing devices and internal systems. Microsoft’s patches target critical Remote Code Execution flaws and privilege escalation vulnerabilities, emphasizing the importance of staying up to date with regular security updates.
Understanding these updates is crucial in protecting enterprise environments. Below, we categorize the vulnerabilities based on their exposure to the internet.
Updates are listed according to their CVSS Score
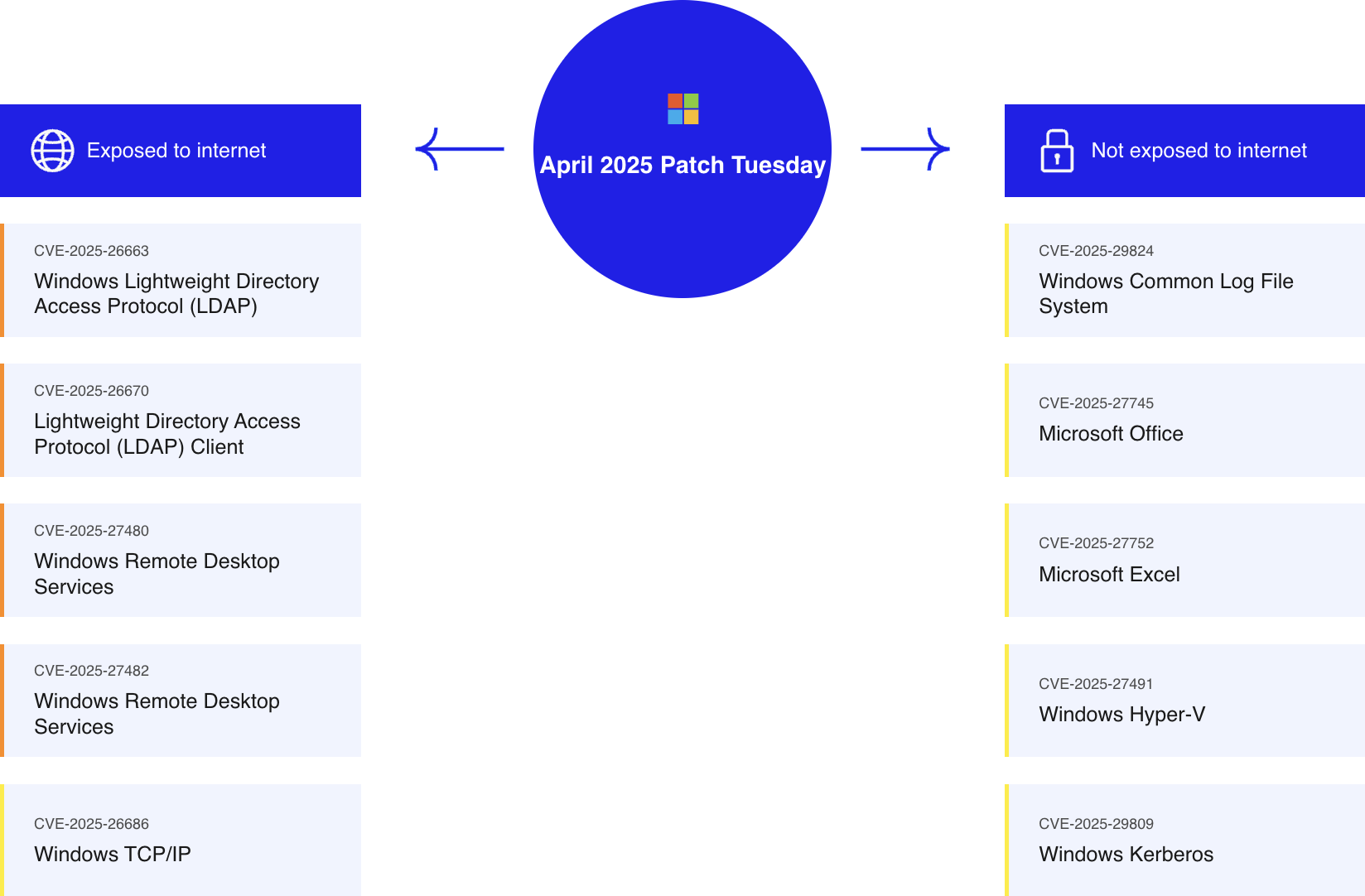
Exposed to the Internet
Windows Lightweight Directory Access Protocol (LDAP) – Remote Code Execution
This vulnerability pertains to the Windows Lightweight Directory Access Protocol, where a use-after-free vulnerability can lead to Remote Code Execution. The issue is unauthenticated, meaning attackers do not need credentials to exploit it, presenting a critical risk in environments relying on LDAP for directory services and authentication.
Windows LDAP Client – Remote Code Execution
The vulnerability exists within the Windows LDAP client. It involves a race condition that allows attackers to execute arbitrary code, posing a serious risk in network environments where LDAP is utilized for authentication and directory services, potentially compromising the security of affected systems.
Windows Remote Desktop Services – Remote Code Execution
This vulnerability affects Windows Remote Desktop Services, causing Remote Code Execution due to improper memory handling. Attackers exploiting this flaw can compromise systems remotely, making it crucial to secure environments using Remote Desktop for remote management or access.
Windows Remote Desktop Services – Remote Code Execution
Also targeting Windows Remote Desktop Services, this vulnerability enables attackers to execute malicious code remotely by exploiting a race condition. Ensuring protective measures against this vulnerability is vital for maintaining the integrity and security of remotely accessible systems.
Windows TCP/IP – Remote Code Execution
This vulnerability affects Windows TCP/IP with a memory management issue that might enable attackers to run malicious code. It underscores the critical need to manage and patch vulnerabilities in networking protocols to safeguard against remote exploits.
Internal Network
Windows Common Log File System – Elevation of Privilege
This vulnerability affects the Windows Common Log File System (CLFS) and is a user-after-free vulnerability. It allows attackers to elevate their privileges to SYSTEM, making it a significant threat to system security. Exploiting this issue could enable unauthorized users to gain elevated access and potentially control over the affected system. Microsoft Threat Intelligence Center (MSTIC) Identified that a threat actor is exploiting this vulnerability to deploy ransomware against targets such as organizations in various locations and verticals.
Microsoft Office – Remote Code Execution
A vulnerability in Microsoft Office allows attackers to execute code through a specially crafted file, illustrating the critical importance of careful handling of Office files from untrusted sources. Successful exploitation can compromise the affected Office application and potentially the entire system.
Microsoft Excel – Remote Code Execution
A heap overflow vulnerability in Microsoft Excel can be exploited to allow remote code execution, leading to potential threats where Excel is ubiquitous in processing spreadsheet data. This underlines the necessity for caution when opening Excel files from unverified sources.
Windows Hyper-V – Remote Code Execution
A use-after-free vulnerability in Microsoft’s hardware virtualization allows for remote code execution, posing a serious risk within virtualized environments. This vulnerability highlights the importance of securing virtualization solutions to prevent potential breaching and control over virtual machines.
Windows Kerberos – Security Feature Bypass
A flaw in Windows Kerberos security- an authentication protocol that is used to verify the identity of a user or host, that allows attackers to bypass security features, potentially leading to unauthorized access. Given Kerberos’ role in secure authentication within Windows domains, addressing this vulnerability is crucial to prevent unauthorized entry and potential malicious activity.(read more)
Conclusion
The security of your systems is a continuous journey that requires awareness of vulnerabilities and prompt patching. While some vulnerabilities exploit applications exposed to the internet, others focus on internal threats. Regularly updating systems is the best defense against these security challenges.
Have questions about implementing these patches or securing your IT environment? Schedule a call with At-Bay’s Advisory Services team to get started.
About CVSS
The Common Vulnerability Scoring System (CVSS) is an industry-standard framework for evaluating and communicating the severity of software vulnerabilities. It provides a numerical score that helps organizations prioritize and address security issues effectively. CVSS scores quantify the severity of a vulnerability on a scale from 0 (no severity) to 10 (critical severity). CVSS considers multiple factors, including; Exploitability, Impact, Exploit code maturity, Remediation level, Report confidence. The system enables organizations to compare and prioritize vulnerabilities based on their potential impact on IT infrastructure.
Read More
- https://msrc.microsoft.com/update-guide/releaseNote/2025-Apr
- https://www.bleepingcomputer.com/news/microsoft/microsoft-april-2025-patch-tuesday-fixes-exploited-zero-day-134-flaws/
- https://blog.talosintelligence.com/microsoft-patch-tuesday-april-2025/
- https://www.tripwire.com/state-of-security/april-2025-patch-tuesday-analysis
- https://www.rapid7.com/blog/post/2025/04/08/patch-tuesday-april-2025/
- https://community.spiceworks.com/t/topic/1194574
- https://krebsonsecurity.com/2025/04/patch-tuesday-april-2025-edition/
- https://www.crowdstrike.com/en-us/blog/patch-tuesday-analysis-april-2025/
- https://www.helpnetsecurity.com/2025/04/08/patch-tuesday-microsoft-zero-day-cve-2025-29824/
- https://www.microsoft.com/en-us/security/blog/2025/04/08/exploitation-of-clfs-zero-day-leads-to-ransomware-activity/